Azure Deployment
The image shows a possible architecture of walt.id Enterprise deployed in the Azure Cloud.
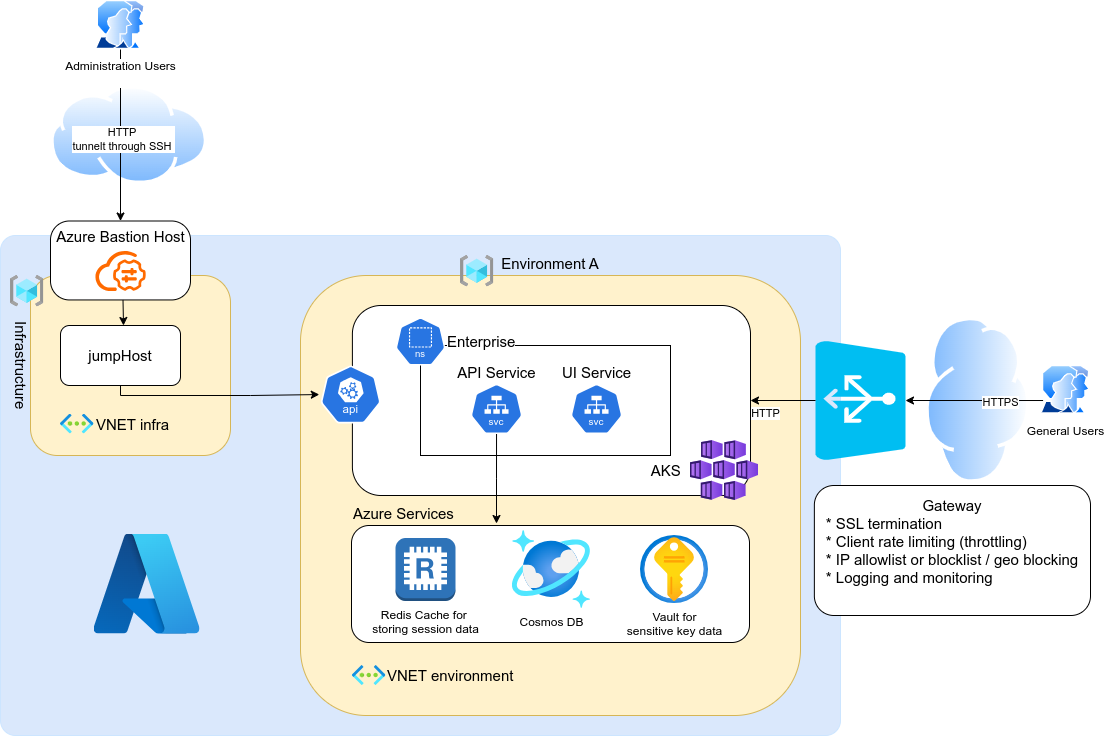
Infrastructure
This infrastructure is optional. It is needed when you deploy AKS or CosmosDB Cluster in private mode (not public accessible)
- Bastion: All sensitive endpoints are not publicly exposed. In order to connect to internal services,you need to connect to the jumphost via the bastion first. If you want to restrict access of some user to internal service, you just need to revoke access to the bastion. The user might still possess credentials for the services, but can not log on, because he cannot connect to the service.
- JumpHost: This is a linux vm which serves as SOCSK5 proxy by tunneling through SSH connection.
- VNET: A VNET which connects the bastion with the jumpHost. The vnet is peered with all environment VNETs
Walt.Id Environment
- AKS: Hosts the Walt.Id Enterprise service
- Application Gateway: Exposes Walt.id Enterprise service to public. In Azure are several options available.
- CosmosDB Mongo
- VNET: The VNET connects CosmosDB, AKS and Application Gateway
This is only one possible architecture. The Walt.Id Enterprise Service can be easily integrated in any already existing Azure Cloud infrastructure.
Terraform examples can be provided, which demonstrates how to set up enterprise stack.
Last updated on November 4, 2025
